| Summary: This blog shares tips to protect data and discusses how data breach is more critical than it is perceived to be. |
|---|
An individual’s personal data is being processed and accessed every second – in the form of card and digital payments, at work, in dealing with public authorities and offices, for medical procedures, for travel bookings, or during something as regular as surfing the internet. Most individuals, however, are usually unfamiliar with the risks of the data breach. Data Privacy Day is observed in order to sensitize individuals and disseminate privacy practices and principles. Whether it’s an internet user, a consumer, or privacy personnel, the onus of safeguarding privacy lies with every individual.
What is a Data Breach?
With the advancement of technology, much of our personal information has been moving to digital. A data breach is a security incident where information is accessed without authorization, affecting individuals and businesses in many ways. Online crime, a result of a data breach, is a threat to anyone on the Internet. It can often damage lives and reputations. The data breach is a growing concern for both individuals and business organizations.
Breach, defined as ‘an act of breaking’, is an attack on one’s cyber data. By breaking into your personal and valuable information to access your confidential and personal identification details like personal health information, PINs, social security numbers, bank details, credit card details, intellectual property, trade secrets, etc, cyberattacks are becoming increasingly common.
Cyber attacks lead to compromised personal data that can easily be viewed, transmitted, or copied for nefarious activities by fraudsters, hackers, and spies. Cybercrimes often occur due to spear-phishing, accessing not-so-secure website/payment gateways, accessing your private chats and profiles on social media apps like WhatsApp, Facebook, Instagram, etc, opening suspicious emails that lure you with monetary rewards. In 2016, Leoni AG lost $44 million in an email scam.
‘Data leak’, ‘Data spill’ are some other terms of data breach
Stories of massive data breach pops up in the news frequently these days. 2020 witnessed some alarming data breach and cyber-attacks. On January 22, Microsoft disclosed a data breach from December 2019. In a blog post, Microsoft said a change made to the database’s network security group on December 5, 2019, contained misconfigured security rules that enabled exposure of the data. According to ZDNet, the servers contained 250 million entries, with information such as email addresses, IP addresses, and support case details.
In 2020, the Covid-19 induced pandemic pushed organizations and businesses to transition most of their work to remote working, making the use of digital and technological tools even more prominent than earlier. It meant more digital exposure and adoption of technology.
The data breach that affected India in 2020
- Twitter Data Breach: On July 15, 2020, a small number of employees were targeted through a phone spear-phishing attack. This attack relied on a significant and concerted attempt to mislead certain employees and exploit human vulnerabilities to gain access to our Twitter’s systems. The knowledge gained through the attack enabled the frauds to target additional employees who had access to the Twitter account support tools.
- Unacademy Data Breach: In January 2020, Bengaluru-based online education platform, Unacademy’s over 20 million user accounts were exposed. The cyberattack bared usernames, SHA-256 hashed passwords, date joined, last login date, email addresses, first and last names, and whether this account is active, a staff member, or a super-user and was sold on Dark Web. The data breach was exposed by US-based cybersecurity firm Cybele.
- BigBasket User Data Breach: Cybercriminals attacked the online grocery store, BigBasket, in October 2020. Data of 20 million subscribers was exposed as a result. The personal information of users such as full names, email addresses, date of birth, IP addresses of user devices got compromised and was put up on sale on the dark web for $40,000.
- Juspay Data Breach: The Bengaluru-based payment entity was attacked in August 2020. As per the details shared by the company, a system where the data was stored by the company was exposed in a cyberattack and over 3.5 crore records with masked card data and card fingerprint (which is non-sensitive information) were breached.
Reasons for Data Breach
Online usage soared in the year 2020 with the on-going coronavirus pandemic. As the pandemic forced people to confine themselves to their houses, digital proceedings grew. It gave scammers an opportunity to launch phishing attacks. Cybercrime is a profitable industry that continues to grow and in the recent situation, it has become easier. A data breach occurs when a cybercriminal successfully infiltrates a data source and extracts sensitive information. It can be done physically by accessing a computer or network to steal local files or by bypassing network security remotely. Hackers seek personal information to steal money, compromise identities, or sell details over the dark web. The reasons for data breach could be many, including accidental sharing of data. But attackers usually work in these four ways:
- Exploiting system vulnerabilities: Finding loopholes in out-of-date software, company’s security systems including computer networks and people. It allows a cybercriminal to slip malware onto a computer and steal data.
- Network or Social Attacks because of weak passwords: Weak and insecure user passwords are easy to guess and get access into personal systems. Experts advise against simple passwords.
- Drive-by downloads: It refers to the unintentional download of a virus or malicious software (malware) onto your computer or mobile device. An unintended download can take advantage of a browser, app, or operating system that is out of date and has a security flaw.
- Targeted malware attacks: A malware attack is a common cyberattack where malware (malicious software/virus) executes unauthorized actions on the victim’s system. It encompasses many specific types of attacks such as ransomware, spyware, command and control, and more. Attackers use spam and phishing email tactics to trick users into revealing personal credentials, downloading malware attachments, or directing users to vulnerable websites. Malware attack is most common in the form of suspicious emails.
How to protect personal information in cases of a data breach?
India ranks third in terms of the highest number of internet users in the world after the USA and China, according to the government of India’s Niti Aayog. The number has grown six-fold between 2012-2017 with a compound annual growth rate of 44%. The country also secures a spot amongst the top 10 spam-sending countries in the world alongside the USA. Ranked among the top five countries to be affected by cybercrime by online security firm ”Symantec Corp”, it becomes imperative to understand the ways to protect personal data.
To begin with, everyone should be aware of the methods used to breach data and keep oneself abreast of data privacy tips to make sure any information is not compromised. Some of the ways to protect data include:
Secure Home Routers
The Internet router is one of the most important devices in our home, the gateway to Internet access. But it is also prone to exploits by cybercriminals who can sneak into our devices and get access to our system. A strong password may avoid unnecessary use of your Wi-Fi by neighbours, but isn’t enough to protect you from cyber attackers. To secure your home network, change the name of your Wi-Fi network, also known as the SSID (Service Set Identifier), activate network encryption, and change your default IP address. Additionally, use a virtual private network. A VPN will encrypt all traffic leaving your devices until it arrives at its destination. If cybercriminals do manage to hack your communication line, they won’t intercept anything but encrypted data.
Strong Passwords
It all begins with weak passwords. Usually, a strong password consists of alphabets, numerical and special characters with the combination of both uppercase and lowercase. Your password should be 10-15 characters. Also, changing your password frequently and never using the same password for multiple platforms helps in a big way.
Never Open Suspicious e-Mails
Even if there is a little doubt about the authenticity of emails, avoid opening it. Cross check the sender’s email ID and open the email only after verifying its authenticity. Always remember to not click on links and advertisements from unknown senders. Emails from retail corporations or banks asking for your details are one of the common ways of data theft. Delete them immediately.
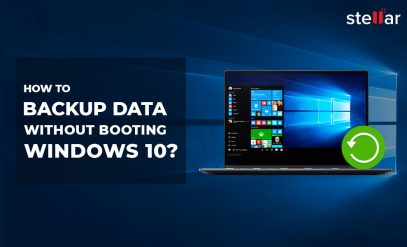
Browse Secure Websites
Always browse websites with HyperText Transfer Protocol Secure (HTTPS) instead of HyperText Transfer Protocol (HTTP). HTTPS ensures that the website is secure enough for browsing and your information is safe. It protects data integrity and provides confidentiality. HTTPS encryption relies on Secure Sockets Layers (SSL), which ensures that anyone in between the sender and the recipient cannot decode the information exchanged.
Avoid Public Wi-Fi
Public Wi-Fi networks are of huge convenience. But it also brings security concerns. Most public Wi-Fis do not have a secure wireless encryption protocol. WPA2 wireless encryption protocol is secure than WEP and WPA, if you have to connect to a public Wi-Fi, always connect to WPA2. Ensure not to sign into your accounts for long.
Secure Your Payments
When you purchase things online or dine out at your favorite restaurant, you opt for point-of-sale (POS) transactions. Point-of-sale completes a transaction and includes receipt printing, credit card processing, etc., and store customer data. This eases the online payment ecosystem. But it also contains weak links that can be exploited. You must validate to ensure that you are swiping your credit card through a safe and secure point-of-sale.
Tip: Make sure that payment provider is Payment Card Industry Security Standards Council (PCI SSC) complaint
Install Anti-virus and Use Updated Software
Update your antivirus and anti-spyware software regularly to prevent virus intrusion or malware attack. It protects you against spyware, keyloggers, Trojans, adware, worms, rootkits etc. To eliminate security vulnerabilities, always install the latest software updates.
Challenges Are Increasing in the Cyber-Space Domain, Protect Your Data
In light of increasing cyber threats, the government has set up initiatives to protect data and is taking stringent actions with cybercriminals. The government has been promising a robust cybersecurity policy. But current laws do not mandate notification of data breach to customers and companies largely tend to report cybersecurity incidents to regulators only where it is mandatory under applicable laws.
There is still a wide gap in data protection regulations that need to be bridged. Threats are increasing with each technological advancement. While we will have to wait for proper data protection regulations to come into effect. At the time, to protect data, it is important to practice data protection tips to avoid a data breaches.