STELLAR® ENCRYPTED DRIVE RECOVERY
Comprehensive and Reliable Encrypted Drive Recovery Solutions
Stellar® provides comprehensive data recovery solutions to help you restore lost and deleted data from encrypted drives. We provide In-Lab data recovery services to recover encrypted data in all data loss situations - be it logical or physical. Our data recovery experts use advanced tools and techniques to restore up to 100% of data from password-protected hard disk drives, SSDs, RAID, USB drives, pen drives, SD cards, and more. We also offer DIY data recovery software to recover data from encrypted drives lost due to any logical reason.

Physically Damaged Encrypted Drive
Data recovery from physically damaged encrypted hard drive, SD card, pen drive, memory stick, or other storage drive requires specialized skills and technology. Contact Stellar® encrypted data recovery services for the safe recovery of data from such drives.
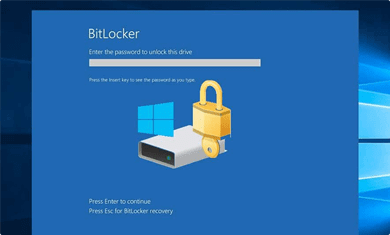
BitLocker-Encrypted Drive
If you have deleted or lost data from BitLocker–encrypted drive or partition, you can use Stellar® Data Recovery software. The DIY tool can easily restore lost or deleted data from BitLocker-encrypted drives and partitions.

File Level Encryption
If your encrypted files are inaccessible, missing, or deleted due to any reason, seek the help of encrypted files recovery services of Stellar®. We ensure all your files are restored with utmost integrity.
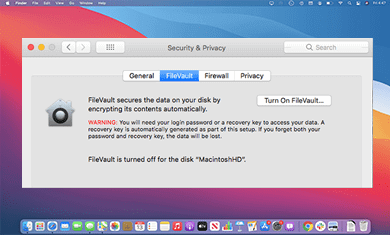
Encrypted Mac Drives
If you’ve lost important data from File Vault-encrypted drives used in macOS X 10.3 later, seek the help of Stellar’s® encrypted data recovery services. We have world-class infrastructure and proprietary technology to restore data from encrypted Mac drives.
BEST ENCRYPTED DRIVE RECOVERY SOLUTIONS
Encrypted Data Recovery in all Data Loss Situations
We provide professional encrypted data recovery services in all data loss scenarios, such as encrypted storage drive failure, ransomware encryption, decrypt error, fatal error, Blue Screen of Death error, Safe Guard/McAfee Safe Boot/PGP/CryptoLocker/Symantec endpoint encryption, and more. Our data recovery professionals can efficiently reinstate your valuable data from encrypted or locked computer drives and external storage media of all types and capacities.
Safe Boot Encryption Errors
Restore data from disk-level Safe Boot encrypted drives and media lost due to file system corruption, bad sectors, drive failures, deletion, overwriting, and more. Our encryption data recovery experts ensure data recovery with complete safety and privacy.

Self-Encrypted Hard Drives
Recover data lost from self-encrypted hard disk drives and SSDs of Toshiba™, Western Digital™, Seagate™, and other brands. The encrypted data recovery experts at Stellar® safely restore all types of files from encrypted hard disk drives.

Ransomware- Encrypted Drives
If you have been hit by a ransomware attack, there is no need to pay huge sum of money to the attacker to unlock the encrypted drive. Simply contact our data recovery experts to recover the data from such encrypted drives.
SAFE & SECURE ENCRYPTED DATA RECOVERY
Recover Data from Encrypted Drives of All Brands
We offer encrypted data recovery solutions for all kinds and capacities of hard drives, SSDs, RAID, memory cards, SD cards, USB, flash drives, pen drives and more. Our data recovery experts can decrypt files in readable form regardless of the make and model of encrypted storage drives. We have a track record of successfully recovering up to 100% data from all well-known brands of storage drives, including Western Digital®, Dell®, Toshiba®, Seagate®, Samsung®, SanDisk®, Kingston®, and others.


World-Class Encrypted Data Recovery Solutions
Drive encryption protects your data by changing it into unreadable code. You can only decrypt the files using a specified secret key. However, disk corruption, ransomware attack, decrypt error, lost encryption key, etc., can result in data loss from these protected storage drives. At Stellar®, we provide the best-encrypted data recovery services and a DIY data recovery software that is designed to recover encrypted files in original form in various logical data loss scenarios.
OUR RECOMMENDATIONS
How to Increase the Success Rate of Data Recovery?
Losing encrypted data is a complicated situation. Any kind of hit and trial technique or unprofessional intervention can lead to permanent data loss. It is recommended not to fiddle with the encrypted systems and external storage media from which you’ve lost the data. Here are some useful tips that can help you to increase the chances of data recovery and avoid irreparable data loss.

Don’t
tamper with encrypted drive
Don’t tamper with the encrypted drive if it is not working. There can be issues such as virus attack, bad sectors on the drive, etc. Tampering can further damage your data and reduce the chances of recovery.

Don’t try to fix damaged hard drive
If your encrypted storage drive becomes inaccessible or gets damaged, do not try to fix it on your own as it may cause further damage. Immediately contact a reliable data recovery service provider to recover data from damaged hard drive.

Don’t try hit & trial methods for decryption
If you have lost the passcode/ PIN/ encryption key, don’t try to decrypt your data repeatedly using hit and trial methods. This can make data recovery impossible. Immediately, contact Stellar’s® encrypted data recovery experts for advice.
FAQ
Yes, our encrypted data recovery experts can help you to restore data in a readable format from self-encrypted Windows and Mac systems.
The encryption key is necessary to recover locked files and folders. If you have lost the encryption key, there are the least chances of data recovery from that drive or media. However, you can contact our encryption data recovery experts, who can guide you based on your unique data loss situation.
Yes, we provide full-disk encryption recovery services, irrespective of the third-party encryption tool you have used.
Encrypted data recovery services cost can be estimated only after proper analysis of affected storage media. It depends upon the data loss situation and the type of damage to your encrypted drive. You can contact Stellar for more details.
Locky is a type of ransomware that follows the classic pattern. It attacks in silence and uses complicated AES – 128 ciphers and RSA encrypting algorithm to lock your personal files. Once it encrypts the data, the data format changes to .locky and becomes inaccessible for the user. The virus scans the system for specific extensions and encrypts them. It mainly targets pictures, music, presentations, documents etc. Also, it encrypts mapped networks and even removable drives if plugged in. It also encrypts Bitcoin wallet files if present, thus making it virtually impossible to use Bitcoins. This virus hides in a Word document and is distributed via spam emails, email attachments, and file sharing networks from unknown senders. The following file types are targeted by the Locky ransomware virus and after encryption all the affected files have the .locky extension: ".sxw, .ott, .odt, .DOC, .pem, .csr, .crt, .key, wallet.dat, .sxc, .ots, .ods, .hwp, .dotm, .dotx, .docm, .docx, .DOT, .max, .xml, .txt, .CSV, .uot, .RTF, .pdf, .XLS, .PPT, .stw, .mid, .wma, .flv, .mkv, .mov, .avi, .asf, .mpeg, .vob, .mpg, .wmv, .fla, .swf, .wav, .qcow2, .vdi, .vmdk, .vmx, .gpg, .pot, .pps, .sti, .sxi, .otp, .odp, .wks, .xltx, .xltm, .xlsx, .xlsm, .xlsb, .slk, .xlw, .xlt, .xlm, .xlc, .dif, .stc, .jpg, .tif, .tiff, .NEF, .psd, .cmd, .bat, .class, .jar, .java, .asp, .brd, .sch, .dch, .dip, .vbs, .asm, .pas, .cpp, .sldm, .sldx, .ppsm, .ppsx, .ppam, .docb, .mml, .sxm, .otg, .odg, .uop, .potx, .potm, .pptx, .pptm, .std, .sxd, .aes, .ARC, .PAQ, .tar.bz2, .tbk, .bak, .tar, .tgz, .rar, .zip, .djv, .djvu, .svg, .bmp, .png, .gif, .raw, .cgm, .jpeg, .php, .ldf, .mdf, .ibd, .MYI, .MYD, .frm, .odb, .dbf, .mdb, .sql, .SQLITEDB, .SQLITE3, .asc, .lay6, .lay, .ms11 (Security copy). It is always suggested to not open any malicious files or links.
Unfortunately, if your computer has been infected by ransomware, then there is no way to decrypt the encrypted files. Even a powerful antivirus scan can't fix the affected files. When this ransomware gets installed as an executable, it begins to encrypt the files. The personal information of the user is locked out by the virus as it changes the format of the data. It then installs some .exe files and makes the user believe that paying the ransom is the only way out to recover the files back. A Tor website named Locky Decrypter is where the user is expected to pay. Even if the users are willing to pay a hefty amount of money, the chances of recovering files are negligible. The best way to regain files is to seek the help of professional data recovery experts. They keep a tab on the latest virus/ransomware and develop tools and techniques to effectively recover data for the customers.
Follow the below-mentioned points to ensure your computer system is safe from any possible ransomware attack:
- Never open an email attachment from an unknown source
- Always update your antivirus programs
- Ensure security is up-to-date
- Always take backup of your data
 Free Download
Free Download  Buy Now
Buy Now