Data in the wrong hands can cause havoc.
In 2018, Marriott International, one of the world’s largest hotel chains, suffered a crippling data breach. It exposed the details of almost 400 million customers, including addresses, phone numbers, and credit card numbers.
Credit: theguardian.com
The breach cost Marriott $72 million. Facebook to Yahoo to Sony Pictures - all large businesses have been a victim of lax data security. Knowing how to protect confidential data is essential for businesses and individuals alike. A competitor would like to know more about your expansion plans, projected revenue, and other sensitive matters. Your personal data is equally crucial.
How to protect confidential data? We teach you the best practices.
Why is Data Protection Essential?
- Protect business plans
A rival can learn the innermost details about your future plans by stealing a laptop. As an entrepreneur, you depend on the element of surprise. If the business strategy is known beforehand, it compromises your future.
-
Protect financial details
How much have investors put into your business? How much borrowing have you taken on and on what terms? What percent of your equity are you going to dilute? That information displays how leveraged you are. A business that has taken on more loans than it can handle is vulnerable to a hostile takeover and acquisition.
- Protect IP
The protection of intellectual property is one of the most important aspects of data protection. Your competition would like nothing better than to steal your design and process and clone it.
Besides the above, the more obvious reason to protect data is that it is private.
No one would like the rest of the world to know too much. You might not have any objection to your banker knowing all about your financial problems, but definitely don’t want your address to be floating around on the internet. Learning how to protect personal data would pay rich dividends.
How to Protect Confidential Data?
-
Manage Data
Manage data because you need to know exactly where it is and where the copies are. Knowing that it is somewhere on the office server and if you want an aide can navigate to it is not enough. You have to know the exact location of the folder, the number and names of the folders, and where copies are maintained.
Being lax is going to prove expensive because the more the copies, the greater the possibility of being compromised. Only authorised personnel must have access to data. Something meant for the CFO should not be accessible to his assistant.
- Use File Encryption
You must have heard of encryption by now. Encryption is securing a file with a specific key. It is nothing new and has been around since the time of the Crusades. The easiest way to encrypt a file is to use archival software like WinRAR. Maintain all files in the same folder and use a strong password.
-
Use Secure Password
Most overlook the need for a safe and secure password. To make it easier to remember, users set up something like their dog’s name followed by the year when their mother was born. Needless to say, that is easily cracked. Hackers use what is known as brute-force attack. Theoretically, it can crack open any password, but the more complex the password, the longer it takes.
Let's test some out using Password Monster.
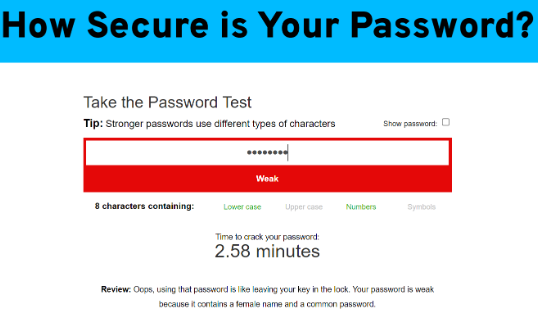
Credits: passwordmonster.com
- emmy2020 would take 2.58 minutes to crack.
- But insert a little complexity and make it emmy@2020 and the time taken rises to 25.75 minutes.
- Change it to Noob@2020 and it would take 3 days!
- The reason—“emmy” is a known word but not “noob”
- Moreover, “Noob” has a mix of upper and lower case and a special character @
A nice trick is to add +- to all keywords to up the time taken to 3 years. After all, two more special characters are that much harder.
-
Use VPN
When you connect your device to the internet, it is akin to opening the door of your house and stepping out on the street. But if you had an underground tunnel that led you a mile away, no one could come in through the front door of your house since you are not going to use it. A VPN or virtual private network is a digital tunnel (quite literally) between your device and a server on another continent that allows you to connect to the wider world anonymously. Always use VPN if you are using an unknown network to log in (such as a hotel or cafe).
- Use Apps With End-to-End Encryption
Encrypted messaging apps are indispensable for maintaining secrecy. There is little sense in protecting data when it can be easily intercepted in transit. When sending files, use messaging systems that are highly secure and nothing else. WhatsApp, Signal, and iMessage are end-to-end encrypted. Otherwise, you can send encrypted files using email, but send the key through messaging systems.
- Update OS
You would be surprised at the number of enterprises that run Windows 7 because they have legacy hardware and software issues. Windows 7 support ended in January 2020. After support ends, no security patches are issued for the operating system. Using an out-of-date operating system, antivirus and browser are akin to extending an open invitation to hackers and laying out the red carpet. Even if you do not suffer an overt data breach, a ransomware attack would happen sooner or later. Make sure that the device and the software on it are recent and safe to use.
- Be Cautious About Device Disposal
This is of paramount importance and deserves its own section. As experienced professionals, we never cease to be amazed by how blase, even experienced entrepreneurs, are about device disposal. A cursory “reset to factory settings” and their Pixel 6 Pro is out and replaced by a brand new iPhone 13. That does nothing to erase data, just as a format does not destroy data from USB or hard drives.
All it does is remove files, but it does not erase them. Note the difference. The file table is removed and no one can navigate to the file anymore. That does not mean the file is gone. It’s like removing the library catalogue but keeping the books intact.
How to protect private data when you dispose, sell, or donate your old laptop, desktop, hard drive, mobile or other storage device?
What you need is BitRaser?
BitRaser is made with cutting-edge technology. BitRaser guarantees that every bit in every block is erased securely. It wipes the entire disk in compliance with HIPAA, GDPR, ISO 27001, PCI DSS, and other international data eraser standards.
Features of BitRaser (That Make It Numero Uno)
- Erases hard drives of desktops, laptops, and servers.
- Erases external drives, internal drives, and USB drives.
- Works with both Mac and Windows, 32 and 64-bit systems.
- Supports all interfaces—PATA, SATA, NVME, PCI, SAS, SCSI, IDE.
- Issues tamper-proof certificates and generates reports for an audit trail. Check sample data eraser report here.
- Install on bootable USB and run to simultaneously erase 32 drives.
BitRaser is an excellent tool for data erasure and should always be your first choice before letting used hardware out of your sight.




