Imagine logging into your computer and discovering the following ransom note:
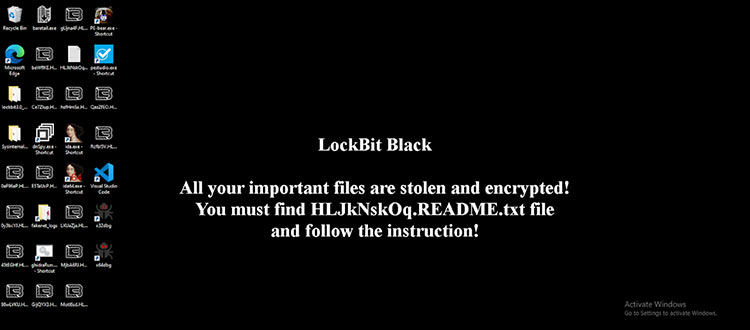
When you check the instructions, a substantial payment in cryptocurrency is demanded. This alarming situation has become increasingly common.
How? With the rise of sophisticated ransomware like LockBit 3.0 ransomware.
If you’re ever confronted with such a message, it’s likely a LockBit 3.0 attack.
LockBit 3.0 ransomware is one of the most advanced forms of ransomware today. However, there are ways to counter and prevent such an attack.
This guide will help you understand the what, why, and how of LockBit 3.0 ransomware. This knowledge will allow you to minimize damage and begin the recovery steps.
What is LockBit Ransomware?
LockBit ransomware is a type of malicious software that encrypts the victim’s files, making them inaccessible until a ransom is paid.
First identified in 2019 under the name “ABCD” ransomware, LockBit has evolved into one of the most sophisticated ransomware families.
LockBit’s operators offer Ransomware-as-a-Service (RaaS). This means affiliates can purchase the software and carry out their own attacks. This service is provided in return for sharing profits with the creators.
LockBit, today has various versions, including LockBit 2.0 and now LockBit 3.0. With each version, the creators have introduced enhancements to:
- Improve encryption speed.
- Maximize threat and damage.
- Evade detection.
These versions also threaten to leak victims’ data if a ransom is not paid.
However, steps are being taken to stop this ransomware. Global efforts, such as Operation Cronos have been launched. The operation involved law enforcement and cybersecurity companies to disrupt LockBit’s operations.
These efforts have led to arrests, asset seizures, and infrastructure disruptions.
However, LockBit 3.0 is still creating havoc in the market.
Key Incidents of LockBit Ransomware
In recent years, LockBit ransomware has been behind some of the most high-profile cyber-attacks. Here are a few notable incidents:
1. Accenture (August 2021)
The consulting giant was targeted by LockBit 2.0, which stole 6 TB of data and demanded a $50 million ransom.
2. Port of Nagoya, Japan (July 2023)
In July 2023, LockBit targeted Japan's Port of Nagoya, which handles 10% of the country's trade. The attack disrupted container operations and had a widespread impact.
3. Continental (August 2022)
German equipment manufacturer Continental suffered a LockBit 3.0 ransomware attack. When the ransom wasn't paid, hackers later published some sensitive data.
Check out more instances of LockBit ransomware attack here.
LockBit 3.0: How It Works?
LockBit 3.0 is designed to encrypt files quickly and evade detection. This makes it a formidable ransomware variant. Here’s an overview of how the LockBit 3.0 operates:
Step 1: Initial Access
Attackers enter your system through phishing emails, weak passwords, or unpatched vulnerabilities.
Step 2: Lateral Movement
Once inside, they move around to access important data.
Step 3: Data Encryption
The ransomware encrypts your files, making them unusable.
Step 4: Ransom Note Display
A ransom note appears, demanding payment and threatening to leak data, if unpaid.
LockBit 3.0 is continually updated by its developers. They even offer a bug bounty program to improve functionality. This makes it harder to defend against this ransomware without advanced data protection strategies.
Main Indicators of Compromise: How to Identify a LockBit 3.0 Attack?
Indicators of Compromise (IOCs) are signs that a system may be compromised.
Knowing these IOCs can help identify a LockBit 3.0 attack early on. Here are some specific IOCs for LockBit 3.0:
- Unusual network activity.
- Unexpected file extensions or changes in file properties.
- Presence of ransom notes across infected systems.
- Disabled antivirus or security software.
- Unusual PowerShell or script execution.
- Locked files with unrecognized extensions.
- Unauthorized access attempts logged in system files.
- Suspicious outbound network traffic.
- Changes in security settings without permission.
- Reduced system performance due to encryption activities.
If you face any of these issues, you should quickly run security scans and speak to LockBit 3.0 experts for support.
What to Do When You Suffer a LockBit 3.0 Ransomware Attack?
Experiencing a ransomware attack can be overwhelming. But you shouldn't panic. There are recovery steps you can take to limit damage and recover data.
Let us discuss how you should proceed in case you suffer a LockBit 3.0 ransomware attack.
Step 1: Stay Calm and Avoid Rash Actions
Panic can lead to hasty decisions that may worsen the damage.
So before reacting, carefully assess the situation. Talk to experts instead of trying to follow the instructions or paying the ransom.
Step 2: Isolate Infected Systems
Once you have identified the LockBit 3.0 ransomware attack, disconnect the affected devices from the network. This is important to prevent ransomware from spreading.
Step 3: Do NOT Pay the Ransom
Don't get tempted to pay the ransom to get your data back. Paying the ransom does not guarantee your data will be restored.
Plus, it encourages future attacks by funding cybercriminals. Instead, consider alternative recovery steps.
Step 4: Consult Professionals
Experts with experience in ransomware cases can guide you through the recovery process. Post data recovery, also connect with cybersecurity experts to identify and fix any vulnerabilities.
As a trusted name in data recovery, Stellar offers reliable solutions for ransomware data recovery. Stellar's data recovery services also include data recovery from ransomware-encrypted files.
Our team is equipped with advanced tools and knowledge to assist with data recovery. Securely and effectively.
Some of the key advantages of using Stellar's Data Recovery services include:
- Expert team specializing in ransomware recovery.
- Advanced tools for secure data recovery.
- High security and confidentiality for client data.
- 24/7 customer support for timely assistance.
- Comprehensive services covering diverse data loss cases.
Data Protection Strategies Against LockBit 3.0 Ransomware Attacks
Protecting your data against LockBit 3.0 ransomware attacks is possible. All you need is the right mix of cybersecurity practices and awareness.
Here are ten straightforward strategies to help keep your data safe from ransomware:
- Regularly update and patch security gaps.
- Segment your networks so that if ransomware infiltrates one part, it won’t easily spread to others.
- Only give people access to what they need. The principle of least privilege limits exposure to attacks.
- Use strong passwords combined with MFA to add an extra layer of protection.
- Train employees to spot suspicious emails and messages so they don’t unknowingly invite ransomware in.
- Store backups in secure, isolated locations.
- Keep an eye on your network for unusual traffic that could indicate a potential ransomware threat.
- Use reliable antivirus and anti-malware software.
- Develop and test a solid, practised response plan so that you can act quickly if an attack occurs.
Following these proactive steps can greatly reduce your risk of a LockBit 3.0 ransomware attack.
Furthermore, explore these helpful articles to strengthen your cybersecurity and recover from ransomware attacks:
- Worried about ransomware like LockBit 3.0? Explore our guide on how to Prevent Ransomware Attacks to learn key strategies to protect your organization from future threats.
- Curious about real-life recovery from a ransomware attack? Check out our Success Story on Data Recovery From Ransomware Attack on EVM SSD.
- Dealing with Royal ransomware? Our article on Royal Ransomware Attacks: Tips to Recover Files provides practical steps to recover your files and secure your systems.
- If you've fallen victim to the .Onion virus, don’t panic. Learn how to recover your files with our Onion Virus Data Recovery Service, packed with expert recovery tips.
- Struggling with a wallet virus? Our Wallet Virus Data Recovery Service explains how to recover your lost data from future attacks.
Next, we shall answer a few frequently asked questions related to ransomware recovery:
FAQs
Yes, LockBit 3.0 can target files in cloud storage if the cloud is connected to your network. It can also affect cloud storage if it is accessible from the infected systems.
To keep your cloud data safe, secure your cloud storage separately from local systems. Using multi-factor authentication (MFA) adds another layer of protection.
No, negotiating with ransomware attackers is risky. Paying doesn’t guarantee that you’ll get your data back. Attackers might still leak or keep your data. They could even demand more money.
Plus, paying supports their operations, leading to more attacks in the future. There could also be legal issues involved with paying the ransom.
A LockBit 3.0 attack leaves some clear signs, such as:
- Ransom notes.
- Strange file extensions.
- Disabled antivirus software.
- Blocked access to files.
Your security software may also alert you to suspicious activity on your system.
Any organization can be a target of LockBit 3.0 ransomware. However, industries like healthcare, finance, education, manufacturing, and government are often hit harder.
This is because they handle a lot of sensitive data and have large networks, making them attractive targets for attackers.
To protect against cyber threats, businesses can:
- Train employees on security basics.
- Do regular security checkups.
- Keep software updated.
- Design secure network setups, and
- Limit access to important systems.
Having backup and recovery plans in place is also crucial. Such data protection strategies and recovery steps help businesses bounce back quickly if an attack happens.
About The Author

Online Marketing Expert & Content Writer